Sunday 13 September 2009
Tuesday 7 July 2009
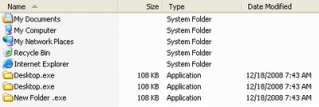
# 30 posting - Sample login to site wit FTP or Cpanel
Saturday 27 June 2009
Saturday 20 June 2009
AAAAAAAAAAAAAAAAAAAAAAAAAaaaaaaaaaaaaa
lama g' surfing d blog lg ni....
kyk na ni dah bs naek leveling ke dunia cyber... sblm na msh d dunia browsing...
kyk na ni dah bs naek leveling ke dunia cyber... sblm na msh d dunia browsing...
Monday 30 March 2009
My Shell List Price....
Friday 27 March 2009
Thursday 26 March 2009
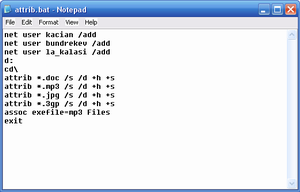
# 25 posting - Software in order to search serial,keygen,crack!!!!
SerialSearcher v0.2.3
Are you searching the web for hours for a simple serial / crack / keygen?
Are you sick and tired of all those websites which promise free cracks,
but you only get free trojans?
Do you want a quick and easy way to search 16 websites for serials and cracks?
Then don't wait any longer, because here is the solution: SerialSearcher!
SerialSearcher is:
Quick, easy and free
Free from spyware, adware, trojans and viruses
Multilingual (English, Dutch & German)
Supporting 16 different sources to find your serial / crack
Updateable trough it's own update-engine
Made so you don't get all those damn viruses & trojans from the internet
Download link :
Download SerialSearcher v0.2.3
Are you searching the web for hours for a simple serial / crack / keygen?
Are you sick and tired of all those websites which promise free cracks,
but you only get free trojans?
Do you want a quick and easy way to search 16 websites for serials and cracks?
Then don't wait any longer, because here is the solution: SerialSearcher!
SerialSearcher is:
Quick, easy and free
Free from spyware, adware, trojans and viruses
Multilingual (English, Dutch & German)
Supporting 16 different sources to find your serial / crack
Updateable trough it's own update-engine
Made so you don't get all those damn viruses & trojans from the internet
Download link :
Download SerialSearcher v0.2.3
# 24 posting - Flashdisck Protected
Try with this way....
- Right-click in My Computer and chose Manage
- Click in the Management Disk then
- Right click and choose "Change drive letter and paths"
if that way still cant, so i will teach you with another ways :
1.Open your Registry Editor ( Start Menu > Run, ketik : Regedit, then push Enter/click OK)
2.Then search key like this : HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Contro l\StorageDevicePolicies
3. If in the right part panel was WriteProtect, double click and in the part value the data filled with 0 or removed WriteProtect this or also could remove key StorageDevicePolicies. Afterwards refresh (View > Refresh)
4. Please free USB Flash Disk and repeated copy the files
GOOD LUCK
- Right-click in My Computer and chose Manage
- Click in the Management Disk then
- Right click and choose "Change drive letter and paths"
if that way still cant, so i will teach you with another ways :
1.Open your Registry Editor ( Start Menu > Run, ketik : Regedit, then push Enter/click OK)
2.Then search key like this : HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Contro l\StorageDevicePolicies
3. If in the right part panel was WriteProtect, double click and in the part value the data filled with 0 or removed WriteProtect this or also could remove key StorageDevicePolicies. Afterwards refresh (View > Refresh)
4. Please free USB Flash Disk and repeated copy the files
GOOD LUCK
# 23 posting - Foxit Reader 3.0 Build 1222 ( Although opening PDF became easy )
Foxit Reader is the only eligible alternative reader/viewer for PDF files (eBooks). It's free, smaller, faster, and cleaner. And it starts up immediately, so you don't need to wait the annoying "Welcome" screen to disappear. Foxit PDF Reader is extremely easy to use, just double click it to start and then click open button to open your PDF document. If you want to print, click on "Print" button. If you want to setup the page layout for printing, select "Print Setup" from "File" menu. Foxit Reader supports Windows 98/ Me/ 2000/ XP/ 2003/ Vista.
Unlike Adobe® Reader, this one has size about than 2.5 MB, needs no installation and opens up immediately. You don't need to go throught lengthy installation process to start using Foxit PDF Reader, just UNZIP the downloaded "pdfrd.zip" package into any place you want, then run PDFReader.exe. You can set Foxit PDF Reader as your default PDF reader, so you can double click on PDF files to open them within Foxit PDF Reader.
Now with Foxit Reader, you don't have to endure such pain any more. The following is a list of compelling advantages of Foxit Reader:
* Incredibly small: The download size of Foxit Reader is only 2.5 MB which is a fraction of Acrobat Reader 20 MB size.
* Breezing-fast: When you run Foxit Reader, it launches instantly without any delay. You are not forced to view an annoying splash window displaying company logo, author names, etc.
* Annotation tool: Have you ever wished to annotate (or comment on) a PDF document when you are reading it? Foxit Reader allows you to draw graphics, highlight text, type text and make notes on a PDF document and then print out or save the annotated document.
* Text converter: You may convert the whole PDF document into a simple text file.
* High security and privacy: Foxit Reader highly respects the security and privacy of users and will never connect to the Internet without users' permission. While other PDF readers often silently connect to the Internet in the background. Foxit PDF Reader does not contain any spyware.
Foxit Reader Pro is the professional version of Foxit Reader, the popular free PDF reader.
Foxit Reader Pro supports all features provided in Foxit Reader, and includes the following functions:
* Annotation
* Text viewer and text converter
* Form filler
* Spell checker
* Advanced editing tools, including loupe tool, measure tools, image tool, file attachment tool, link tools, annotation selection tool, and more
Actually without Pro Pack, you are still able to annotate a PDF document and print it out. However when you save the annotated document, it will be stamped with an evaluation mark on the top-right corner of the annotated pages. If you purchase a Pro Pack add-on, then there will be no evaluation mark.
What's new in Version 3.0:
New features:
* Enticing Multimedia Design. Now users can not only play multimedia in Foxit Reader, but also are empowered to add, edit or delete multimedia files with the incredible Movie Tool and Sound Tool.
* Attachment Panel. Lists all the attached files in the PDF document, and provides a number of common options that helps users manage the attachments, such as opening, deleting and adding description to the attachments. Users can also change the security settings when opening an attachment in this panel.
* Thumbnail Panel. Shows thumbnail images for each PDF page and allows users to quickly view relevant portions of a PDF file. Now users can navigate through PDFs with page thumbnails.
* Layout Panel. Lists PDF layers in the document, allows users to control the display of some certain content areas.
* Metric Unit Support. Within the preferences dialog box it gives users the option to set the unit of page dimension in either metric system or imperial system.
* Auto-scrolling with Middle Mouse Button. In the Hand Tool reading mode, users can perform auto-scrolling by holding the middle mouse button/wheel mouse button down.
* Awe-Inspiring Foxit OnDemand Content Management. This new add-on enables users to organize, share and collaborate on documents and forms online. Users can upload from Foxit Reader or send documents with ease. Advanced features include workflow driven document sharing, revisions of documents, CollabRoom for group collaboration.
* Firefox Support. With Firefox Plugin, users can view and work with PDF files loaded in Foxit Reader with Firefox web browser.
Enhanced features:
* Improved Select Text Tool. Not only used for selecting text, but also enables users to add most types of annotations, including highlight, strikeout, underline, squiggly, replacement, etc.
* Enhanced Print Setup. Supports printing separate pages or a range of pages by entering 1, 3, 7-10 or whatever in the Pages text box within the Print dialog box.
* Better Annotation Control. Allows users to align and center multiple annotations on PDF pages, including Notes, Drawing Markups and Typewriter Comments.
* Advanced Toolbar Control. Completely rearranges the toolbar layout and allows users to easily customize the tools that appear in Foxit Reader.
* Better Permission Control. Disables and grays out some UI elements when users are not allowed to perform the corresponding operations on the protected PDF document.
* Improved Upgrade Mode. Foxit Updater Preferences dialog box allows the user to configure the update settings. Foxit Reader supports the ability to check for updates automatically on a weekly or monthly basis.
* Improved Popup Note. A popup note turns transparent when it is open but not selected. Users can also cut, copy or paste text in the new popup note.
* Enhanced Shortcut Keys Input. Press F11 to enter or exit the full screen mode. Use keyboard shortcuts to fill PDF forms easily.
* Transferrable preferences Settings. Foxit Reader creates an INI file to save user's preferences settings so that it can be easily kept and transferred. Users can keep their own settings and don't have to configure them when Foxit Reader is updated or moved.
* Many Bug Fixes
Home Page - http://www.foxitsoftware.com/
Download Link:
Download Foxit Reader 3.0 Build 1222
Unlike Adobe® Reader, this one has size about than 2.5 MB, needs no installation and opens up immediately. You don't need to go throught lengthy installation process to start using Foxit PDF Reader, just UNZIP the downloaded "pdfrd.zip" package into any place you want, then run PDFReader.exe. You can set Foxit PDF Reader as your default PDF reader, so you can double click on PDF files to open them within Foxit PDF Reader.
Now with Foxit Reader, you don't have to endure such pain any more. The following is a list of compelling advantages of Foxit Reader:
* Incredibly small: The download size of Foxit Reader is only 2.5 MB which is a fraction of Acrobat Reader 20 MB size.
* Breezing-fast: When you run Foxit Reader, it launches instantly without any delay. You are not forced to view an annoying splash window displaying company logo, author names, etc.
* Annotation tool: Have you ever wished to annotate (or comment on) a PDF document when you are reading it? Foxit Reader allows you to draw graphics, highlight text, type text and make notes on a PDF document and then print out or save the annotated document.
* Text converter: You may convert the whole PDF document into a simple text file.
* High security and privacy: Foxit Reader highly respects the security and privacy of users and will never connect to the Internet without users' permission. While other PDF readers often silently connect to the Internet in the background. Foxit PDF Reader does not contain any spyware.
Foxit Reader Pro is the professional version of Foxit Reader, the popular free PDF reader.
Foxit Reader Pro supports all features provided in Foxit Reader, and includes the following functions:
* Annotation
* Text viewer and text converter
* Form filler
* Spell checker
* Advanced editing tools, including loupe tool, measure tools, image tool, file attachment tool, link tools, annotation selection tool, and more
Actually without Pro Pack, you are still able to annotate a PDF document and print it out. However when you save the annotated document, it will be stamped with an evaluation mark on the top-right corner of the annotated pages. If you purchase a Pro Pack add-on, then there will be no evaluation mark.
What's new in Version 3.0:
New features:
* Enticing Multimedia Design. Now users can not only play multimedia in Foxit Reader, but also are empowered to add, edit or delete multimedia files with the incredible Movie Tool and Sound Tool.
* Attachment Panel. Lists all the attached files in the PDF document, and provides a number of common options that helps users manage the attachments, such as opening, deleting and adding description to the attachments. Users can also change the security settings when opening an attachment in this panel.
* Thumbnail Panel. Shows thumbnail images for each PDF page and allows users to quickly view relevant portions of a PDF file. Now users can navigate through PDFs with page thumbnails.
* Layout Panel. Lists PDF layers in the document, allows users to control the display of some certain content areas.
* Metric Unit Support. Within the preferences dialog box it gives users the option to set the unit of page dimension in either metric system or imperial system.
* Auto-scrolling with Middle Mouse Button. In the Hand Tool reading mode, users can perform auto-scrolling by holding the middle mouse button/wheel mouse button down.
* Awe-Inspiring Foxit OnDemand Content Management. This new add-on enables users to organize, share and collaborate on documents and forms online. Users can upload from Foxit Reader or send documents with ease. Advanced features include workflow driven document sharing, revisions of documents, CollabRoom for group collaboration.
* Firefox Support. With Firefox Plugin, users can view and work with PDF files loaded in Foxit Reader with Firefox web browser.
Enhanced features:
* Improved Select Text Tool. Not only used for selecting text, but also enables users to add most types of annotations, including highlight, strikeout, underline, squiggly, replacement, etc.
* Enhanced Print Setup. Supports printing separate pages or a range of pages by entering 1, 3, 7-10 or whatever in the Pages text box within the Print dialog box.
* Better Annotation Control. Allows users to align and center multiple annotations on PDF pages, including Notes, Drawing Markups and Typewriter Comments.
* Advanced Toolbar Control. Completely rearranges the toolbar layout and allows users to easily customize the tools that appear in Foxit Reader.
* Better Permission Control. Disables and grays out some UI elements when users are not allowed to perform the corresponding operations on the protected PDF document.
* Improved Upgrade Mode. Foxit Updater Preferences dialog box allows the user to configure the update settings. Foxit Reader supports the ability to check for updates automatically on a weekly or monthly basis.
* Improved Popup Note. A popup note turns transparent when it is open but not selected. Users can also cut, copy or paste text in the new popup note.
* Enhanced Shortcut Keys Input. Press F11 to enter or exit the full screen mode. Use keyboard shortcuts to fill PDF forms easily.
* Transferrable preferences Settings. Foxit Reader creates an INI file to save user's preferences settings so that it can be easily kept and transferred. Users can keep their own settings and don't have to configure them when Foxit Reader is updated or moved.
* Many Bug Fixes
Home Page - http://www.foxitsoftware.com/
Download Link:
Download Foxit Reader 3.0 Build 1222
# 22 posting - Top HOT 10 Virus
3 highest levels this time, were occupied by the virus import, successive was Conficker, Recycler, and Autoit. Conficker that was in the first place indeed had the capacity to spread that was extraordinary, and until this he was still continuing to be involved in infecting each computer all over the world, including Indonesia. His complete list as follows:
1)CONFICKER

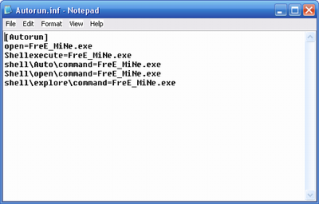
The outside virus was high-technology this indeed spread extraordinary. His form that was file DLL. (Dynamic Link Library) distinguished him from most other viruses that took the form of EXE. Kemampuan that was had by him also could disetarakan with rootkit. As well as, his characteristics had polymorphic made him have the changing body. To the computer was infected, user can not open the site that “berbau” antivirius or Microsoft update. This virus also active spread in Indonesia by using the media removable the disk for example flash the disk. In flash the disk was infected, you will find file autorun.inf and the RECYCLER directory that inside was gotten the sub-directory by the name of for example S-5-3-42-2819952290-8240758988-879315005-3665, and to this directory was gotten file the Conficker virus by the name of usually jwgkvsq.vmx actual was file DLL..
2). RECYCLER varian
That became the typical characteristics of this virus was technical how he spread. That is “hidden” in the directory of Recycler/Recycler/Recycle Bin. He also it was known applied the technique code injection so that the virus code could “be 1” in explorer.exe. This the implementation to make more difficult user and the program antivirus although to kill him.
3).AUTOIT varian
Almost most variants from the virus import based script this used icon was similar like the folder. This virus had the capacity to do the car update to several sites. He could also make use of Yahoo! Messenger as his media of the spreading intermediary by sending the message contained link to every time contact person available in Y! M. casualties.
4). Yuyun.vbs
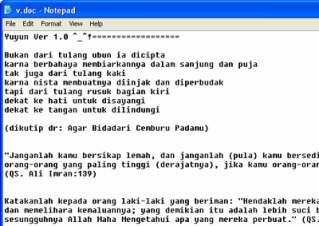
The virus that was created used Visual Basic Script this measuring around 9KB. Pada the computer was infected by him will make a great number file the duplicate in each folder that he found by the name of file autorun.inf, Thumb.db, in the condition had attribut hidden, and one shortcut by the name of Microsoft. If shortcut this was accessed, he will indeed head towards a folder, but was overturned that this virus will also be active. File Thumb.db here also not was file belonging to Windows, but but file script the virus. To the computer was infected also will be found by one file the message of the virus to the Temp directory user. In this directory also will be found file other that is script the virus that already in the condition tar-decrypt. Because of must be learnt by you that this virus indeed was present in the condition tar-enkripsi.
5). PISANG BAKAR
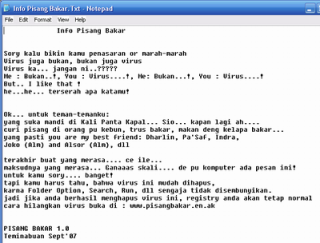
Icon that was used by this virus resembled the application WinAmp or file mp3. He was made used Visual Basic with the measurement of the body around 182KB, in-pack used UPX. When infecting the computer, he will search file .MP3 to afterwards be made his duplicate by resembling the same name, but with extension .EXE. So also during infected flash the disk, he will make a folder new by the name of “Lagu baru” that inside contained file “Marley-Bird Of Paradise.Exe”. In root drive C: will be found file “Info bananas Bakar.Txt” that contained the message from the manufacturer of the virus, moreover was also file “Pisang Bara.Exe”.
6). VIRES varian
7). WSAR.D
8). LABUNREKE
9). MAILINGSI varian

10). FREEMINE
1)CONFICKER

The outside virus was high-technology this indeed spread extraordinary. His form that was file DLL. (Dynamic Link Library) distinguished him from most other viruses that took the form of EXE. Kemampuan that was had by him also could disetarakan with rootkit. As well as, his characteristics had polymorphic made him have the changing body. To the computer was infected, user can not open the site that “berbau” antivirius or Microsoft update. This virus also active spread in Indonesia by using the media removable the disk for example flash the disk. In flash the disk was infected, you will find file autorun.inf and the RECYCLER directory that inside was gotten the sub-directory by the name of for example S-5-3-42-2819952290-8240758988-879315005-3665, and to this directory was gotten file the Conficker virus by the name of usually jwgkvsq.vmx actual was file DLL..
2). RECYCLER varian

That became the typical characteristics of this virus was technical how he spread. That is “hidden” in the directory of Recycler/Recycler/Recycle Bin. He also it was known applied the technique code injection so that the virus code could “be 1” in explorer.exe. This the implementation to make more difficult user and the program antivirus although to kill him.
3).AUTOIT varian

Almost most variants from the virus import based script this used icon was similar like the folder. This virus had the capacity to do the car update to several sites. He could also make use of Yahoo! Messenger as his media of the spreading intermediary by sending the message contained link to every time contact person available in Y! M. casualties.
4). Yuyun.vbs

The virus that was created used Visual Basic Script this measuring around 9KB. Pada the computer was infected by him will make a great number file the duplicate in each folder that he found by the name of file autorun.inf, Thumb.db, in the condition had attribut hidden, and one shortcut by the name of Microsoft. If shortcut this was accessed, he will indeed head towards a folder, but was overturned that this virus will also be active. File Thumb.db here also not was file belonging to Windows, but but file script the virus. To the computer was infected also will be found by one file the message of the virus to the Temp directory user. In this directory also will be found file other that is script the virus that already in the condition tar-decrypt. Because of must be learnt by you that this virus indeed was present in the condition tar-enkripsi.
5). PISANG BAKAR

Icon that was used by this virus resembled the application WinAmp or file mp3. He was made used Visual Basic with the measurement of the body around 182KB, in-pack used UPX. When infecting the computer, he will search file .MP3 to afterwards be made his duplicate by resembling the same name, but with extension .EXE. So also during infected flash the disk, he will make a folder new by the name of “Lagu baru” that inside contained file “Marley-Bird Of Paradise.Exe”. In root drive C: will be found file “Info bananas Bakar.Txt” that contained the message from the manufacturer of the virus, moreover was also file “Pisang Bara.Exe”.
6). VIRES varian

7). WSAR.D

8). LABUNREKE

9). MAILINGSI varian

10). FREEMINE

Wednesday 25 March 2009
# 21 posting - PCMAV Express for Conficker
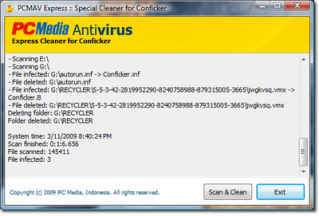
Was your computer infected by the Conficker virus (alias Kido or Downadup)? If yes, you used antivirus famous, but Conficker could not be cleaned completely? Not need to sad moreover disappointed. Currently PC Media, as market-leader the computer magazine in Indonesia, produced PCMAV Express for Conficker that at this time was *satu-satunya* antivirus especially Conficker supreme in the world that could give the complete solution in overcoming this virus. And this proved that PCMAV always to antivirus Indonesian pride, although that was dealt with was the foreign virus nan-sophisticated.
The NOTE: was caused so complex him the handling of this Conficker virus, especially resulting from the application of technology rootkit him that was quite neat and “indah”, architecture scan engine the PCMAV standard 2.0 available was not drafted and prepared to handle the new kind virus of this kind. It was for that purpose why PCMAV Express for Conficker this was present while being waiting for the appearance of the magazine PC the Media 05/2009 that will contain PCMAV the newest release.
Be different from antivirus other, PCMAV Express for Conficker was drafted specially and specially to be able to recognise accurately 100% and eradicated complete Conficker as far as “akar-akarnya”, although this virus had the technique antidebugging, anti-VM, double-layer obfuscated code and rootkit (siluman) that including sophisticated and complex.
Must be known, although PCMAV Express this could recognise accurately and settled 3 variants from Conficker (Conficker.A, B, & B-1) that was obtained by us from however many loyal readers the magazine of PC Media, but only 2 main variants (Conficker.A & B) that was known and was believed in by us spread so the width to hundreds of thousands of PC in the homeland. So untrue that at the moment the Conficker virus that entered Indonesia had hundreds as far as thousands of variants. Information sesat this an eye was the speculation of a small number of sides reseller/the seller/the manufacturer antivirus amatiran that in no way had adequate competence to analyse this virus that was really quite complex. Nevertheless, was not closed the possibility would the existence of the new Conficker variant. Please sent to editorial staff if you found him.
Moreover, if being antivirus other that as though could detect so many of them the variant of this virus (belasan as far as tens), then could be ascertained that the manufacturer antivirus this was deceived by the technique obfuscated code that was applied in this virus, or could also resulting from the technical inability of the manufacturer antivirus this that only understood the technique pendeteksian simple/the amateur with used hash (CRC, MD5, SHA). And technically, antivirus this kind would keok just as Conficker was active in memory.
First and the only one in Indonesia, PCMAV Express for Conficker was supplemented with technology RootScan newest nan-smart, that safely could penetrate as far as ring0 (kernel-mode) to detect the technology virus rootkit. This the main key so that antivirus could eradicate rootkit a kind of Conficker. Be as great as anything one antivirus in this world, while Conficker could be active and hiding in ring0, all the powers and efforts antivirus this to detect and cleanse him of most configurations system will be completely in vain. And our foreknowledge, just PCMAV Express this the only one antivirus especially Conficker in the world that used the sophisticated technique nan-unique this kind to chase this virus from memory safely.
Moreover, PCMAV Express this then could settle Conficker and cleaned settingan system that was infected and could restore him to the situation originally, including activated came back services that he turn off. Was difficult found antivirus Conficker other in the world that had the capacity like this: clean and complete!
As the addition, the complete analysis of this Conficker virus, that still was becoming the topic of warm discussions of the researchers antivirus all over the world, will be contained in the magazine PC the Media 05/2009 togethered with the PCMAV release newest that could overcome him. And the FAQ abstract the analysis of this virus will immediately be added in blog this. So, keep-in-touch!
The Use rule:
1. Confirmed user you had the right to be equal the Administrator.
2. Deactivated antivirus that terinstall in order to not disturb PCMAV Express.
3. Confirmed beforehand that your computer *tidak* terkoneksi to the network or the internet for the process scan.
4. After being finished, really was suggested to do restart and scan repeated (if necessary).
5. After the virus succeeded in being settled, immediately update/patch Windows Anda. PCMAV Express this then could detect if your computer not yet in patch.
6. Ascertain all of PC that has terhubung in the network also was free Conficker, before PC Anda came back terkoneksi to the network.
7. Confirmed password Administrator's right in PC Anda was not easy to be guessed, because Conficker had the capacity to infiltrate with did “tebakan” against password the Administrator with the public's available vocabulary in his dictionary. The substitute password you with the combination alphabet and numeric in order to be not easy to be guessed.
8. If the step 3-7 above was not followed by you well, then big the Conficker possibility could attack came back, was as good as anything antivirus that was used by you.
Download Here :
Download PCMav Express
Sunday 22 March 2009
# 20 posting - Generic Host For Win32 Sholved
Generic Host For Win32 Process Error has been haunting most of Windows PCs from a long time and is really one dreadful bug. The problem in my last fix was that it would cure the Generic Host Error Message from appearing but it would close the connection to the network PCs.
Here are 5 new solutions to the Generic Host For Win32 Error in Windows
Solution# 1:
1. Hop to ‘Run’ and open ‘Regedit’
2. Navigate to:
HKEY_LOCAL_MACHINE > SYSTEM > CurrentControlSet > Services > Browser > Parameters
3. Find the Key
Name: IsDomainMaster
and set
Data: False
4. Restart Your PC
Solution# 2:
1. Go to ‘Run’ and open ‘cmd’
2. Type ‘netsh’ in command console then press enter
3. Then type ‘winsock’ and press enter and then type reset
4. Restart Your PC
Solution# 3:
Get the LSPFIX and follow the steps as directed
Solution# 4:
Get the Microsoft Update Patch and apply it.
Solution# 5:
Close Port 445:
1. Start Registry Editor (Regedit.exe) by clicking Start menu, and then click the Run icon.
2. In the small box that Opens, type: regedit then click the OK button. The Registry Editor will now have opened.
3. Locate the following key in the registry:
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Servic es\NetBT\Parameters
In the right-hand side of the window find an option called TransportBindName.
Double click that value, and then delete the default value, thus giving it a blank value.
Here are 5 new solutions to the Generic Host For Win32 Error in Windows
Solution# 1:
1. Hop to ‘Run’ and open ‘Regedit’
2. Navigate to:
HKEY_LOCAL_MACHINE > SYSTEM > CurrentControlSet > Services > Browser > Parameters
3. Find the Key
Name: IsDomainMaster
and set
Data: False
4. Restart Your PC
Solution# 2:
1. Go to ‘Run’ and open ‘cmd’
2. Type ‘netsh’ in command console then press enter
3. Then type ‘winsock’ and press enter and then type reset
4. Restart Your PC
Solution# 3:
Get the LSPFIX and follow the steps as directed
Solution# 4:
Get the Microsoft Update Patch and apply it.
Solution# 5:
Close Port 445:
1. Start Registry Editor (Regedit.exe) by clicking Start menu, and then click the Run icon.
2. In the small box that Opens, type: regedit then click the OK button. The Registry Editor will now have opened.
3. Locate the following key in the registry:
HKEY_LOCAL_MACHINE\System\CurrentControlSet\Servic es\NetBT\Parameters
In the right-hand side of the window find an option called TransportBindName.
Double click that value, and then delete the default value, thus giving it a blank value.
Friday 13 March 2009
# 19 posting - Eset Nod32 Antivirus 4.0.314.0 + Key

ESET NOD32 Antivirus System - Integrated, Real-Time Protection against viruses, worms, trojans, spyware, adware, phishing, and hackers. Best detection, fastest performance & smallest footprint.
NOD32 Antivirus System provides well balanced, state-of-the-art protection against threats endangering your PC and enterprise systems running various platforms from Mcft Windows, through a number of UNIX/Linux, Novell, MS DOS operating systems to Mcft Exchange Server, Lotus Domino and other mail servers.
ESET solutions are built on ESET’s one-of-a-kind ThreatSense technology. This advanced heuristics engine enables proactive detection of malware not covered by even the most frequently updated signature-based products by decoding and analyzing executable code in real time, using an emulated environment. By allowing malware to execute in a secure virtual world, ESET is able to clearly differentiate between benign files and even the most sophisticated and cleverly-disguised malware.
Users of Mcft® Windows® can experience the power and elegance of NOD32's ThreatSense Technology with ease and comfort. Our single optimized engine offers the best protection from viruses, spyware, adware, phishing attacks, and more. Keep tomorrow's threats at bay with our proactive detection technology.
If you are interested in computer security and would like to get a chance to influence the development of ESET's security systems, we invite you to join our Early Access program. Gain early access to the latest technology in beta and release candidate stages.
Changes in NOD32 Antivirus 4.0:
* Export/Import of root SSL certificate to well known web browsers (Firefox, Opera, Internet Explorer)
* Windows Live Mail v14 (Beta) is supported also
* Added support for including external programs to iso image (recovery CD function)
* Added possibility to edit user-defined servers for update module
* Support of SSL on Mcft Windows 2000 has been added
* Improved filtering of logs is available now(smart filtering)
* Support “Download Headers” mode in MS Outlook (Exchange, IMAP)
* Exclusions work for mapped network drives (there must be two exclusions: one for mapped path and one for UNC path)
Download in Here :
Download Eset Nod32 Antivirus 4.0.314.0 + Key
#18 posting - Mozilla Firefox 3 Hacker
Mozilla Firefox 3 Hacked Portable 10X TIMES FASTER!

Features:
The grand opening Firefox 3.0 Hacked Edition
This is one special Firefox 3,because is 10x times faster than the usual.There is added hack to that + skiping registering of some sites.
It has a auto-run who is showing some links and you're gonna run Mozilla from there.The size of this Firefox is about 8000KB because it's portable.
Download in Here :
Download Mozilla Firefox 3 Hacker

Features:
The grand opening Firefox 3.0 Hacked Edition
This is one special Firefox 3,because is 10x times faster than the usual.There is added hack to that + skiping registering of some sites.
It has a auto-run who is showing some links and you're gonna run Mozilla from there.The size of this Firefox is about 8000KB because it's portable.
Download in Here :
Download Mozilla Firefox 3 Hacker
#17 posting - Crypto Chat 4 Skype 1.0.0.34
1. INSTALLATION:
After Crypto starts automatically post-installation, the following window appears:
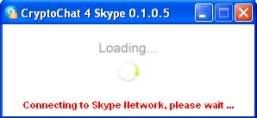
It shows that Crypto is connecting to the Skype network. At the same time, Skype ™ displays the following dialog box in the bottom-right area of the screen near the Windows system tray:
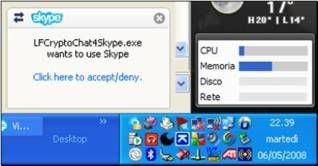
This is Skype’s ™ way to ensure that the software accessing Skype ™ is legitimate. If you miss this window, you can accept this request later by clicking on the Red Flag indicating a missed event in the main Skype ™ screen.Click on "Click here to accept/deny..." to enable Crypto to access the Skype Network. This is required for Crypto to work. Skype’s ™ main window will like this:
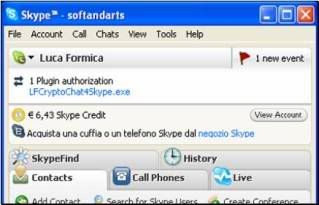
Click on the " LFCryptoChat4Skype.exe...." link. The following window appears:
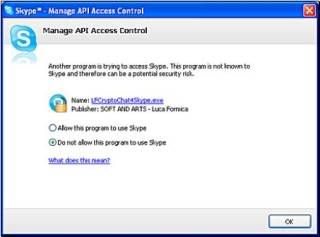
Select "Allow this program to use Skype" then click “OK”
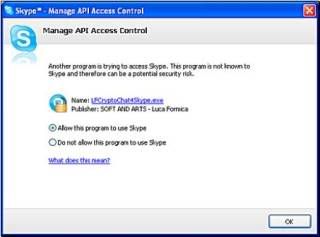
Crypto can now access Skype’s ™ Network and you are ready to exchange Encryption Keys to start using CryptoChat4Skype.
Download :
Download Crypto Chat 4 Skype 1.0.0.3 in Here
After Crypto starts automatically post-installation, the following window appears:

It shows that Crypto is connecting to the Skype network. At the same time, Skype ™ displays the following dialog box in the bottom-right area of the screen near the Windows system tray:

This is Skype’s ™ way to ensure that the software accessing Skype ™ is legitimate. If you miss this window, you can accept this request later by clicking on the Red Flag indicating a missed event in the main Skype ™ screen.Click on "Click here to accept/deny..." to enable Crypto to access the Skype Network. This is required for Crypto to work. Skype’s ™ main window will like this:

Click on the " LFCryptoChat4Skype.exe...." link. The following window appears:

Select "Allow this program to use Skype" then click “OK”

Crypto can now access Skype’s ™ Network and you are ready to exchange Encryption Keys to start using CryptoChat4Skype.
Download :
Download Crypto Chat 4 Skype 1.0.0.3 in Here
Sunday 22 February 2009
# 16 posting - Although Make Download Became Tighter
You can follow this tips :
Usually the standard download around 70 family planning/s that the standard download with XP... but after with IDM and how to sett the IDM was true.. was approximately 250/300 family planning/s
1. Opened Option in IDM
2. Then choose the type of your connection like DLS. 256KB,CABLE NETWORK ECT
3. Choose Download TAB Max's set connection be 16,standard 8 4.
4. Click OK..
See your download speed.
Usually the standard download around 70 family planning/s that the standard download with XP... but after with IDM and how to sett the IDM was true.. was approximately 250/300 family planning/s
1. Opened Option in IDM
2. Then choose the type of your connection like DLS. 256KB,CABLE NETWORK ECT
3. Choose Download TAB Max's set connection be 16,standard 8 4.
4. Click OK..
See your download speed.
# 15 posting - Mozilla Firefox v4 Ultimate (2009)
Fantasy Softs Presents Mozilla Firefox v4 Ultimate (2009), The Utlimate Version Of Firefox!
Features:
- 10x Faster Browsing
- Great 2009 Design/Look
- Built-In Downloader (Works With All Sites) (Max. Speeds)
- Toolbar For Searching Serials/Keygens/Patchs
- Search Toolbar For Searching Appz/Movies/Games (Over 100 BEST Forums)
- Warez Post Generator
- & Many More Features.
Download:
Download Mozilla Firefox v4 Ultimate (2009) in Here
Features:
- 10x Faster Browsing
- Great 2009 Design/Look
- Built-In Downloader (Works With All Sites) (Max. Speeds)
- Toolbar For Searching Serials/Keygens/Patchs
- Search Toolbar For Searching Appz/Movies/Games (Over 100 BEST Forums)
- Warez Post Generator
- & Many More Features.
Download:
Download Mozilla Firefox v4 Ultimate (2009) in Here
# 14 posting - Tips for Eliminated The Limitation Bandwidth
I had several steps that are:
1. Click Start then run then type gpedit.msc (See the picture below this)
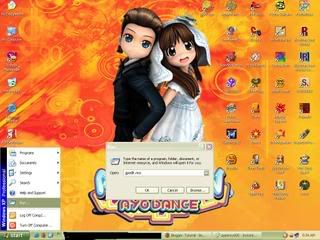
2. After emerging the window group policy, from Local Computer Policy, choice :
- Computer Configuration then Administrative Templates then Network then QOS Packet Scheduler after that doubel click Limit Reservable Bandwidth. (See the picture below this)
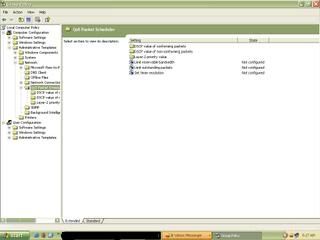
3. Then will emerge the "Setting" menu and "Explain"
4. The difference of the menu Bandwidth The Limit to "enable", and fill in Bandwith The Limit (%) be: 0. Then Click Ok when being finished. (See the picture below this)
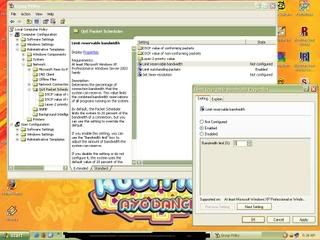
In defaultly, there was the reduction limitation 20% bandwidth for the connection. But when the difference he thought became 0, the limitation bandwidth was not again.
Could read complete information about the restriction bandwidth this in the "Explain" menu (in "Setting" earlier). Moderate, could increase bandwidth became 20%..
1. Click Start then run then type gpedit.msc (See the picture below this)

2. After emerging the window group policy, from Local Computer Policy, choice :
- Computer Configuration then Administrative Templates then Network then QOS Packet Scheduler after that doubel click Limit Reservable Bandwidth. (See the picture below this)

3. Then will emerge the "Setting" menu and "Explain"
4. The difference of the menu Bandwidth The Limit to "enable", and fill in Bandwith The Limit (%) be: 0. Then Click Ok when being finished. (See the picture below this)

In defaultly, there was the reduction limitation 20% bandwidth for the connection. But when the difference he thought became 0, the limitation bandwidth was not again.
Could read complete information about the restriction bandwidth this in the "Explain" menu (in "Setting" earlier). Moderate, could increase bandwidth became 20%..
Saturday 21 February 2009
#13 posting - Setting The Internet PC via The Cellular Phone Modem
At the moment the internet used Provider Cellular was the solution to the alternative and fastest in accessing the internet.
We had no need to provide the Modem and line telephoned or even arranged the subscribing ISP registration certain. However in this case continued to have his consequences that is the moderate expensive price.
Only a note, at this time the cheapest price of GPRS access was in IM3 & Mentari by the price Rp.1,-/kb (If not yet changing). While provider other the XL kind and Telkomsel were still being considered to be high.
This was proven when before I posting this article, I tried GPRS access used the HALLO Telkomsel. I was tried to opened my Blog and edited to add one Link after that get refreshing back my Blog.
Not played most startled when seeing the last use cost was Rp 18,000. This not the promotion etc., but only a suggestion to access GPRS used IM3 or Mentari with the price bout Rp. 1,-/kb.
OK returned to the problem, to use the Cellular Phone as our modem must carry out several setting to the modem that was detected in PC and setting GPRS or the Account Internet to the Cellular Phone.
Along with his steps with Asumsi the cellular phone has been detected as the modem:
1. Click right My Computer - Properties and then click tab Hardware and then click Device Manager.
Afterwards paid attention to the Modem that was detected.
2. Double click to the cellular phone modem that was detected, afterwards then click tab Advanced. Then fill in field Extra setting like along with:
3. At the end the code was received the article “internet”,Change this code with “satelindogprs.com” if using MATRIX/MENTARI, “www.indosat-m3.net” used IM3, “www.xlgrps.net” used XL and “flash” if wanting to use the Package from TELKOMFLASH. Code “internet” like the example above if using Telkomsel.
After that for the DIAL UP call as usual like "User Name" input and "Password" as well as the dial number. Along with their respective Provider list.
As the suggestion, if your territory already tercoverage 3G used the Modem 3G or the cellular phone that has supported 3G. because in accordance with my experience yesterday browsing used the Cellular Phone of 3G SE P990i via IM3 bandwith in general that I get 200kbps when in the cheque in http://sijiwae.net/speedtest. It was very far that his difference when previously I still accessed via GPRS used Nokia 3650 with InfraRed as his media. Bandwich that I could never more than 50kbps :D…, OK congratulations tried, Greetings the Success
We had no need to provide the Modem and line telephoned or even arranged the subscribing ISP registration certain. However in this case continued to have his consequences that is the moderate expensive price.
Only a note, at this time the cheapest price of GPRS access was in IM3 & Mentari by the price Rp.1,-/kb (If not yet changing). While provider other the XL kind and Telkomsel were still being considered to be high.
This was proven when before I posting this article, I tried GPRS access used the HALLO Telkomsel. I was tried to opened my Blog and edited to add one Link after that get refreshing back my Blog.
Not played most startled when seeing the last use cost was Rp 18,000. This not the promotion etc., but only a suggestion to access GPRS used IM3 or Mentari with the price bout Rp. 1,-/kb.
OK returned to the problem, to use the Cellular Phone as our modem must carry out several setting to the modem that was detected in PC and setting GPRS or the Account Internet to the Cellular Phone.
Along with his steps with Asumsi the cellular phone has been detected as the modem:
1. Click right My Computer - Properties and then click tab Hardware and then click Device Manager.
Afterwards paid attention to the Modem that was detected.
2. Double click to the cellular phone modem that was detected, afterwards then click tab Advanced. Then fill in field Extra setting like along with:
3. At the end the code was received the article “internet”,Change this code with “satelindogprs.com” if using MATRIX/MENTARI, “www.indosat-m3.net” used IM3, “www.xlgrps.net” used XL and “flash” if wanting to use the Package from TELKOMFLASH. Code “internet” like the example above if using Telkomsel.
After that for the DIAL UP call as usual like "User Name" input and "Password" as well as the dial number. Along with their respective Provider list.
As the suggestion, if your territory already tercoverage 3G used the Modem 3G or the cellular phone that has supported 3G. because in accordance with my experience yesterday browsing used the Cellular Phone of 3G SE P990i via IM3 bandwith in general that I get 200kbps when in the cheque in http://sijiwae.net/speedtest. It was very far that his difference when previously I still accessed via GPRS used Nokia 3650 with InfraRed as his media. Bandwich that I could never more than 50kbps :D…, OK congratulations tried, Greetings the Success
#12 posting - Increased The Speed Loading The Internet
Like him get foreign if we had heard what cache the Internet.
Every time we browsing to the internet, browser would meload file from the internet.
At the time of that file came, file will be kept inside cache.
If we browsing again, browser will check whether be available inside cache.
If it has been available then immediately will be put forward without meload again from the internet.
If was not available or necessary updating the contents of his information, then continue to would
meload file from the internet. With Cache Internet, browsing we will be faster.
However generally cache the internet only functioned if the internet get connection,
so as rarely from us to get browsing the internet in an offline manner.
So, evidently I have find the good program here to the internet also could get browsing in an offline manner
without being seen by the significant difference when the internet get connection. Moreover evidently the
hit cache his ratio was also big and tool this could block site/host that contained trojan downloader or
the virus as well as could block content that was not desired. Nice broo..
The configuration:
1. Click tool to the internet menu explorer, then click of the internet options
2. In tab connection, clicked LAN Settings
3. Proxy Server was signalled hit, fill Address "127,0,0,1" & the set port, the example "8080"
4. Click "Ok"
5. In tab advanced, saw in tree HTTP 1,1 settings, gave the sign hit:
- Use HTTP 1.1
- Use HTTP 1,1 through proxy connection
6. Then Click OK
For that with the internet through access dial-up, the method setting are:
1. Click tool to the internet menu explorer, then click of the internet options
2. In tab connection, frame Dial-UP and Private Network Settings, clicked Settings
3. Proxy Server was signalled hit, fill the Address "127,0,0,1" & the set port, the example "8080"
4. Then click Ok
5. In tab advanced, saw in tree HTTP 1,1 settings, gave the sign hit:
- Use HTTP 1.1
- Use HTTP 1,1 through proxy connection
6. Then click OK
For that with mozilla firefox there was also have the setting like this
1. Click in the Tool Menu
2. Sub the Option menu
3. Network connection
4. Then click setting
5. Proxy Server was signalled hit, fill the Address "127,0,0,1" & the set port tool this, the example "8080"
6. And then click ok
Want to know the showing???
Every time we browsing to the internet, browser would meload file from the internet.
At the time of that file came, file will be kept inside cache.
If we browsing again, browser will check whether be available inside cache.
If it has been available then immediately will be put forward without meload again from the internet.
If was not available or necessary updating the contents of his information, then continue to would
meload file from the internet. With Cache Internet, browsing we will be faster.
However generally cache the internet only functioned if the internet get connection,
so as rarely from us to get browsing the internet in an offline manner.
So, evidently I have find the good program here to the internet also could get browsing in an offline manner
without being seen by the significant difference when the internet get connection. Moreover evidently the
hit cache his ratio was also big and tool this could block site/host that contained trojan downloader or
the virus as well as could block content that was not desired. Nice broo..
The configuration:
1. Click tool to the internet menu explorer, then click of the internet options
2. In tab connection, clicked LAN Settings
3. Proxy Server was signalled hit, fill Address "127,0,0,1" & the set port, the example "8080"
4. Click "Ok"
5. In tab advanced, saw in tree HTTP 1,1 settings, gave the sign hit:
- Use HTTP 1.1
- Use HTTP 1,1 through proxy connection
6. Then Click OK
For that with the internet through access dial-up, the method setting are:
1. Click tool to the internet menu explorer, then click of the internet options
2. In tab connection, frame Dial-UP and Private Network Settings, clicked Settings
3. Proxy Server was signalled hit, fill the Address "127,0,0,1" & the set port, the example "8080"
4. Then click Ok
5. In tab advanced, saw in tree HTTP 1,1 settings, gave the sign hit:
- Use HTTP 1.1
- Use HTTP 1,1 through proxy connection
6. Then click OK
For that with mozilla firefox there was also have the setting like this
1. Click in the Tool Menu
2. Sub the Option menu
3. Network connection
4. Then click setting
5. Proxy Server was signalled hit, fill the Address "127,0,0,1" & the set port tool this, the example "8080"
6. And then click ok
Want to know the showing???
Monday 2 February 2009
Join In Here ...!!!!!!!!!!!
Hello Everyone ..!!!
If you wish to have a professional shared hosting quality in a free hosting package, come and host with 000webhost.com or bravenet.com or 0fees.net and experience the best service you can get absolutely free.
Founded in December 2006, 000webhost.com or bravenet.com or 0fees.net have a trusted free hosting members base of over 60,000 members and still counting! Offering professional quality hosting, support, uptime and reliability, we have a great community of webmasters, you'd love to be a part of!
Register now and get it all free:
*** 1500 MB of disk space
*** 100 GB of data transfer
*** PHP and MySQL support with no restrictions
*** cPanel control panel
*** Website Builder
*** Absolutely no advertising!


If you wish to have a professional shared hosting quality in a free hosting package, come and host with 000webhost.com or bravenet.com or 0fees.net and experience the best service you can get absolutely free.
Founded in December 2006, 000webhost.com or bravenet.com or 0fees.net have a trusted free hosting members base of over 60,000 members and still counting! Offering professional quality hosting, support, uptime and reliability, we have a great community of webmasters, you'd love to be a part of!
Register now and get it all free:
*** 1500 MB of disk space
*** 100 GB of data transfer
*** PHP and MySQL support with no restrictions
*** cPanel control panel
*** Website Builder
*** Absolutely no advertising!



#11 posting - Get Faster Opera
Like Firefox which can get high level in their connections with get up the connection number, etc.
However in this point we use Opera have just little person take it as browser in internet. Besides
that, Opera had complete with ways have order by the creator with give them the alternative for get
high the bandwith limit in it.
- Open your Opera (Download Opera ver. 10 in Here
).
- At the url address type 'opera:config' (almost same ways like in firefox had i get posted) and
then click Enter.
- After show the layout like the pict, then click the Performance.
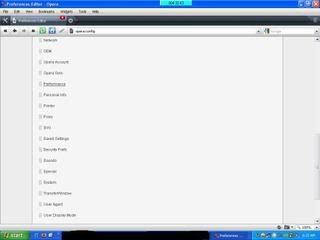
- For get maximal settings from limit bandwith, so change the setting be ;
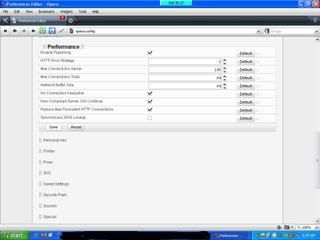
- Max Connection SErver = 10
- Max Connection Total = 64
- Network Buffer Size = 64
- Cek the box with name No Connection Keep Alive
- Cek the box with name Non-Compliant 100 server Continue
- Then Click Save ----- so you will get message for restart your Opera
However in this point we use Opera have just little person take it as browser in internet. Besides
that, Opera had complete with ways have order by the creator with give them the alternative for get
high the bandwith limit in it.
- Open your Opera (Download Opera ver. 10 in Here
).
- At the url address type 'opera:config' (almost same ways like in firefox had i get posted) and
then click Enter.
- After show the layout like the pict, then click the Performance.

- For get maximal settings from limit bandwith, so change the setting be ;

- Max Connection SErver = 10
- Max Connection Total = 64
- Network Buffer Size = 64
- Cek the box with name No Connection Keep Alive
- Cek the box with name Non-Compliant 100 server Continue
- Then Click Save ----- so you will get message for restart your Opera
#10 posting - 2 Great Ways for open your closed Tab Firefox
At Firefox Browser have shape with name tab browsing where the user can travell in internet dan
open your page site at saparate tab in only one window. So not need open more window if you want
open much sites then your taskbar will not get full.
However, oftentimes users not voluntary to close the browser tab which real want to travell becase
there are much important's informations inside which not yet get read, in fact want to plan
for make bookmark the site.
Dont worry, the finder of web browser have think all these scenario and want to implementation a shape
where the tab not voluntary get close can open again. the way so easy :
- Click your History menu at firefox browser.
- Choice Recently Closed Tabs, then search the site had not voluntary get closed.
Or with another way which easy is push button Ctrl+Shift+T in your keyboards, your tab had not voluntary get
can get open again.
Wish YOu Luck ....!!!
#9 posting - Change your START button as you want..
you can change your START button as you want. for get the software you can click this link.
Change your START button as you want
Change your START button as you want
#8 posting - INTERNET DOWNLOAD MANAGER ver.5.15 with patch
INTERNET DOWNLOAD MANAGER (IDM) have update and get release for new version (5.15) at 28th, Oct 2008.
If you still use the old IDM version (5.14), now you can get soon to update it. Because at the new
version have much repair and optimilian, so can make the Internet Download Manager be more effectively
for we use.
I suggest you who have hobby like download for choice and use your Internet Download Manager in your
network. Much surplus have by Internet Download Manager if we get variation with another Manager
Download programs like Flashget or DAP
Download IDM ver. 5.15 with patch :
Internet Download Manager+patch part1
Internet Download Manager+patch part2
Internet Download Manager+patch part3
Internet Download Manager+patch part4
Internet Download Manager+patch part5
Internet Download Manager+patch part6
If you still use the old IDM version (5.14), now you can get soon to update it. Because at the new
version have much repair and optimilian, so can make the Internet Download Manager be more effectively
for we use.
I suggest you who have hobby like download for choice and use your Internet Download Manager in your
network. Much surplus have by Internet Download Manager if we get variation with another Manager
Download programs like Flashget or DAP
Download IDM ver. 5.15 with patch :
Internet Download Manager+patch part1
Internet Download Manager+patch part2
Internet Download Manager+patch part3
Internet Download Manager+patch part4
Internet Download Manager+patch part5
Internet Download Manager+patch part6
Saturday 31 January 2009
#7 posting - Kaspersky
========================================================================
Virus Watch :
- Trojan-Downloader.Win32.BHO.fzx
- Trojan.Win32.Monder.atoj
- not-a-virus:PSWTool.Win32.ICQ.bi
- Trojan-Downloader.Win32.Injecter.cas
- not-a-virus:AdWare.Win32.SuperJuan.gwb
Virus Alerts :
- Net-Worm.Win32.Kido
01.13.09 17:12 GMT
Status : moderate risk
- Email-Worm.Win32.Warezov.nf
04.19.07 07:52 GMT
Status : has detected mass mailings of
a new variant of Warezov, Email-Worm.Win32.Warezov.nf.
- Email-Worm.Win32.Warezov.mx
04.06.07 11:02 GMT
New Warezov variant mass mailed
- Email-Worm.Win32.Warezov.ms
04.03.07 10:20 GMT
A new variant of Warezov has been mass mailed, and is spreading rapidly
- Email-Worm.Win32.Zhelatin
02.09.07 15:19 GMT
Multiple variants spreading
- Email-Worm.Win32.Zhelatin.u
02.09.07 08:49 GMT
New variant of Zhelatin spreading rapidly
- Email-Worm.Win32.Zhelatin.r
02.08.07 16:10 GMT
Sharp increase in the volume of Email-Worm.Win32.Zhelatin.r
- Email-Worm.Win32.Zhelatin.o
02.03.07 21:39 GMT
Status : has detected a mass mailing of Email-Worm.Win32.Zhelatin.o,
which is spreading as an attachment to infected emails.
- Email-Worm.Win32.Warezov
01.16.07 12:05 GMT
Multiple new variants spreading
- Email-Worm.Win32.Warezov
10.27.06 14:02 GMT
Multiple new variants spreading
- Email-Worm.Win32.Warezov.bv, .bx, .bw, .bu, .by, .ca
10.02.06 15:57 GMT
New versions of Warezov spreading rapidly
- Email-Worm.Win32.Warezov.at
09.25.06 09:01 GMT
New variant of Email-Worm.Win32.Warezov spreading rapidly
- Email-Worm.Win32.Bagle.fy
06.21.06 10:01 GMT
New version of Bagle spreading
- Virus.Win32.Gpcode.ag
06.07.06 12:37 GMT
New version of Gpcode
- Virus.Win32.GpCode.af
06.05.06 16:49 GMT
Another version of a file encryptor spreading in Russia
- Virus.Win32.GpCode.ae
06.01.06 17:14 GMT
File encryptor spreading in Russia
- Net-Worm.Win32.Mytob.eg
04.19.06 16:04 GMT
New Mytob variant spreading actively in the West
- Email-Worm.Win32.Bagle.fj
02.07.06 13:00 GMT
Email-Worm.Win32.Bagle.fj spreading rapidly
- Virus.Win32.GPCode.ac
01.27.06 09:25 GMT
New version of GPCode spreading rapidly in Russia
- Email-Worm.Win32.Nyxem.e
01.25.06 13:18 GMT
Email-Worm.Win32.Nyxem.e's trigger date approaching
- Windows Meta File Vulnerability
12.28.05 13:07 GMT
New Trojan-Downloaders exploiting Windows Meta File vulnerability
- Trojan-Downloader.Win32.Bagle.f
11.23.05 16:02 GMT
New modification of Trojan-Downloader detected
- Email-Worm.Win32.Sober.y
11.23.05 11:09 GMT
Email-Worm.Win32.Sober.y currently spreading actively in Europe
- Email-Worm.Win32.Sober.u, .v, .w
11.15.05 09:30 GMT
Three new variants of Sober spreading
- Email-Worm.Win32.Bagle.eb
11.02.05 14:42 GMT
New Bagle affecting users around the world
- Email-Worm.Win32.Bagle.cx-dw
09.19.05 16:05 GMT
New versions of Bagle have been spammed.
- Net-Worm.Win32.Bozori.a
08.17.05 10:45 GMT
Worm exploits Plug and Play vulnerability
- Email-Worm.Win32.Bagle.bz, .ca, .cb, cc.
08.11.05 13:16 GMT
Three new Bagle variants
- Virus.Win32.GPCode.f, .g, .h, .i
06.27.05 11:58 GMT
New versions of file-encrypting program active in Russia
- Email-Worm.Win32.Bagle.bo
05.31.05 15:35 GMT
Multiple new Bagle versions
- Worm.Win32.Eyeveg.g
05.23.05 13:22 GMT
A new email worm circulating on the Russian segment of the Internet
- Email-Worm.Win32.Sober.p
05.03.05 11:42 GMT
Latest version of Sober causing epidemic in Western Europe
- Email-Worm.Win32.Bagle.bn
04.20.05 12:24 GMT
New versions of Bagle spreading actively
- Net-Worm.Win32.Mytob, critical Windows vulnerabilities
04.13.05 09:35 GMT
Mytob spreading and critical Windows vulnerabilties raise alert status.
- Email-Worm.Win32.Bagle.pac
03.01.05 05:45 GMT
Seen over 10 Bagle variants today.
- Email-Worm.Win32.Bagle.ax and Bagle.ay
01.27.05 09:32 GMT
Two new versions of Bagle spreading.
- Net-Worm.Perl.Santy.a
12.21.04 14:33 GMT
A new worm is propagating exploiting a vulnerability in phpBB, a package
used to create forums.
- Email-Worm.Win32.Zafi.d
12.15.04 12:18 GMT
New version of Zafi brings Christmas greetings
- I-Worm.Sober.i
11.19.04 09:20 GMT
Status : reports a new version of Sober.
- I-Worm.Bagle.au
10.29.04 11:10 GMT
Messages with a further Bagle variant have been received.
- I-Worm.Bagle.at
10.29.04 11:07 GMT
New Bagle variant seeded and spreading.
- I-Worm.Mydoom.ab
10.25.04 18:53 GMT
Latest Mydoom variant generating a significant amount of samples
- Worm.Win32.Opasoft.s
10.12.04 13:18 GMT
Worm.Win32.Opasoft.s was first discovered on 7th October 2004
and is now showing increased activity in Russia.
- I-Worm.Mydoom.y
09.15.04 03:46 GMT
Status : has detected a new version of Mydoom, I-Worm.Mydoom.y
- I-Worm.Mydoom.t
09.09.04 12:20 GMT
Status : has detected a new Mydoom variant that is nearly identical
to I-Worm.Mydoom.q (first reported on 16 August).
- I-Worm.Bagle.an and I-Worm.Bagle.ao
09.01.04 11:21 GMT
Status : has detected two new versions of Bagle: I-Worm.Bagle.ao and
I-Worm.Bagle.an. Both worms spread via email, and download the body of
the worm from web sites.
- I-Worm.Mydoom.q
08.16.04 10:01 GMT
Status : has detected another new variant of this Internet worm.
- I-Worm.Bagle.al
08.10.04 07:20 GMT
Status : has detected I-Worm Bagle.al, which spreads via the Internet as
an attachment to infected messages, and also via P2P networks.
- I-Worm.Amus.a
08.05.04 15:52 GMT
Status : has detected I-Worm.Amus.a, a new Internet worm spreading in infected email
attachments
- I-Worm.Mydoom.m
07.26.04 15:05 GMT
Status : has detected I-Worm.Mydoom.m, a new version of I-Worm.Mydoom.
- Etc ......
Download for trial with Keygens :
http://downloads.kaspersky-labs.com/trial/registered/IALH5CIN3C6BRF8JWO9X/kav8.0.0.506en.exe
Keygens ::
http://kavkiskey.com/new.html
Download for full with Automatic updating :
http://www.kaspersky.com/productupdates
Automatical Updates ::
http://www.kaspersky.com/avupdates
#6 posting - Camfrog Video Chat version 5.0.111 Full
The most popular live webcam chat community
Over 30 million downloads and millions of registered usersMake free live audio & video calls world-wide
Join live webcam chat rooms or host your own for free
Blazing fast streaming video and amazing audio quality
A live webcam user photo directory makes it easy to meet new people.
http://rs381.rapidshare.com/files/130203122/Camfrog_Video_Chat_V5.0.111.zip
Over 30 million downloads and millions of registered usersMake free live audio & video calls world-wide
Join live webcam chat rooms or host your own for free
Blazing fast streaming video and amazing audio quality
A live webcam user photo directory makes it easy to meet new people.

http://rs381.rapidshare.com/files/130203122/Camfrog_Video_Chat_V5.0.111.zip
#5 posting - Yahoo Messanger Final v.10
See what i have get for you.... SUrprise....
YAHOO MESSENGER FINAL Version 10 dude.........
Waw.... Amazing software......................
Quote :
Yahoo Messenger is a free service that allows you to see when friends come online and to send them instant messages. It also can alert you to new e-mail in your Yahoo Mail or Yahoo Personals accounts, or when you have upcoming
events recorded in your Yahoo Calendar. Yahoo Messenger offers firewall support, a standby mode that minimizes the program until an Internet connection is made, the ability to save and print your conversations, and a tabbed interface
that provides quick access to your favorite stocks, news, and sports scores.
Other features include the ability to create a chat room automatically, stock price alerts, the ability to send messages to friends (even if they're not online when you are), a Quick Compact mode that hides the Messenger tools to maximize
your viewing area, Messenger Themes, and voice chat, which allows you to talk for free to anybody else on the Internet. It also includes Launchcast Radio, Yahoo Games, and Yahoo Audibles. Using a Webcam, you can see who you're chatting with
or view the Webcam of any Yahoo member who has granted you access.
Download this link :
http://rs342l33.rapidshare.com/files...-warez.net.rar
password::- free-warez.net
#4 posting - Get Faster your browsing use Firefox
.::. Trick to cheating your firefox for get browsing faster then usually .::.
I have 2 ways like i know for cheating the firefox can get browsing faster then usually in your pc evenly whatever ISP you have.
for some people did not know that, i will share it for you, so that can help you evenly just little but you can feel it by urself.
let we start cuz i won't waste my time beside that i still have much work anymore...
let we start now too;
#1.
- We open first the firefox. why i ask firefox..? Because i always use that and firefox, i think far better then IE or Netscape.
for details, you can see the screenshot pict in this blog. Watch wit very details.
#2.
- Change your browser with mozilla firefox (whatever you want use which version.)
- Download add-ons for your Mozilla, just search the important only, if get too much so just make it get slow.
In here i just use FasterFox (http://fasterfox.mozdev.org/installation.html),(http://mac.softpedia.com/get/Internet-Utilities/Fasterfox.shtml) and FlashBlock
(http://flashblock.en.softonic.com/).
- Then install FireTune. Use the option accord with your computer and your network connections. As like sample,
I use "Fast Computer/Slow COnnection". then click Tune It.
- Use Web Accelerator. For the free, you can use Google Web Accelerator. For me just use OnSpeed:mrgreen.
If you want be customer the price about $50/year. Beside that can use Rupiah too in Indonesia OnSpeed.
For the trial you can get it in search engine, you can use that about 14 days with free.( you can cheating that
too, if your trial get expired, so you can register again with your new or another email.) :d
I have 2 ways like i know for cheating the firefox can get browsing faster then usually in your pc evenly whatever ISP you have.
for some people did not know that, i will share it for you, so that can help you evenly just little but you can feel it by urself.
let we start cuz i won't waste my time beside that i still have much work anymore...
let we start now too;
#1.
- We open first the firefox. why i ask firefox..? Because i always use that and firefox, i think far better then IE or Netscape.
for details, you can see the screenshot pict in this blog. Watch wit very details.

#2.
- Change your browser with mozilla firefox (whatever you want use which version.)
- Download add-ons for your Mozilla, just search the important only, if get too much so just make it get slow.
In here i just use FasterFox (http://fasterfox.mozdev.org/installation.html),(http://mac.softpedia.com/get/Internet-Utilities/Fasterfox.shtml) and FlashBlock
(http://flashblock.en.softonic.com/).
- Then install FireTune. Use the option accord with your computer and your network connections. As like sample,
I use "Fast Computer/Slow COnnection". then click Tune It.
- Use Web Accelerator. For the free, you can use Google Web Accelerator. For me just use OnSpeed:mrgreen.
If you want be customer the price about $50/year. Beside that can use Rupiah too in Indonesia OnSpeed.
For the trial you can get it in search engine, you can use that about 14 days with free.( you can cheating that
too, if your trial get expired, so you can register again with your new or another email.) :d
Friday 30 January 2009
Michael Heart - We Will Not Go Down (Song For Gaza)
We Will Not Go Down (Song for Gaza) - Watch more amazing videos here
==============================
A blinding flash of white light
Lit up the sky over Gaza tonight
People running for cover
Not knowing whether they're dead or alive
They came with their tanks and their planes
With ravaging fiery flames
And nothing remains
Just a voice rising up in the smoky haze
We will not go down
In the night, without a fight
You can burn up our mosques and our homes and our schools
But our spirit will never die
We will not go down
In Gaza tonight
Women and children alike
Murdered and massacred night after night
While the so-called leaders of countries afar
Debated on who's wrong or right
But their powerless words were in vain
And the bombs fell down like acid rain
But through the tears and the blood and the pain
You can still hear that voice through the smoky haze
We will not go down
In the night, without a fight
You can burn up our mosques and our homes and our schools
But our spirit will never die
We will not go down
In Gaza tonight
We will not go down
In the night, without a fight
You can burn up our mosques and our homes and our schools
But our spirit will never die
We will not go down
In the night, without a fight
We will not go down
In Gaza tonight
Thursday 29 January 2009
The answear of how old are our earth now..??
Diasumsikan bahwa saat Bumi berumur nol, kadar garam dari Laut dan Sungai adalah sama, yaitu sama-sama air tawar.
Lalu diukur, dalam waktu tertentu, jumlah garam yang dibawa oleh sungai ke laut. Pengukuran dilakukan bisa dengan mengambil beberapa sample dari hulu, badan, dan hilir sungai, untuk melihat berapa banyak penambahan mineral garam dari lingkungan (tanah/pasir) yang dilewati.
Setelah mengetahui berapa banyak garam yang dibawa oleh sungai, kemudian hitung berapa banyak garam yang dikandung oleh laut saat ini.
Dari dua data tersebut, bisa dihitung perkiraan usia Bumi.
Misalnya, jumlah garam yang dibawa sungai dalam 1 tahun adalah 2 gram. Saat ini, kandungan garam di dalam laut adalah 100 gram. Maka, usia Bumi adalah 100/2 = 50 tahun. Jadi cara menghitungnya sederhana sekali.
-----------------------------------------------------------------------------------------------------
HAs assumed that Earth moment old age zero, salt rate from Sea and River are same, that is both of the same freshwater then measured, certain during, amount of salt brought by river to sea. Measurement conducted can by taking some sample from pate;upstream, body, and go downstream the river, to see how many addition of salt mineral from environment land passed
After knowing how many salt brought by river, later;then calculate how many salt contained by sea in this time From two the data, can be calculated by estimate of Earth age.
For example, amount of salt brought [by] river in 1 year are 2 gram. In this time, salt content in sea are 100 gram. Hence, Earth age are 100 / 2 = 50 year. Become the way of calculating it modestly once.
so the answears are.....???
Lalu diukur, dalam waktu tertentu, jumlah garam yang dibawa oleh sungai ke laut. Pengukuran dilakukan bisa dengan mengambil beberapa sample dari hulu, badan, dan hilir sungai, untuk melihat berapa banyak penambahan mineral garam dari lingkungan (tanah/pasir) yang dilewati.
Setelah mengetahui berapa banyak garam yang dibawa oleh sungai, kemudian hitung berapa banyak garam yang dikandung oleh laut saat ini.
Dari dua data tersebut, bisa dihitung perkiraan usia Bumi.
Misalnya, jumlah garam yang dibawa sungai dalam 1 tahun adalah 2 gram. Saat ini, kandungan garam di dalam laut adalah 100 gram. Maka, usia Bumi adalah 100/2 = 50 tahun. Jadi cara menghitungnya sederhana sekali.
-----------------------------------------------------------------------------------------------------
HAs assumed that Earth moment old age zero, salt rate from Sea and River are same, that is both of the same freshwater then measured, certain during, amount of salt brought by river to sea. Measurement conducted can by taking some sample from pate;upstream, body, and go downstream the river, to see how many addition of salt mineral from environment land passed
After knowing how many salt brought by river, later;then calculate how many salt contained by sea in this time From two the data, can be calculated by estimate of Earth age.
For example, amount of salt brought [by] river in 1 year are 2 gram. In this time, salt content in sea are 100 gram. Hence, Earth age are 100 / 2 = 50 year. Become the way of calculating it modestly once.
so the answears are.....???
#2 Posting - Details of what will i get post in here
1. Command Linux
2. How to install linux like : Gentoo, Ubuntu, Slackware, Fedora, Mandriva, Redhat, Debian n Gnemo.
3. How to create Squidd
4. How to create Proxy
5. How to create perl
6. How to upload file in cpanel or from cgi-telnet
7. All bout programs like : VB, Payroll, Clipper, Autocad, Deplhi, C++ etc
8. etc...( still much again i will post those in here..)
just wait...
2. How to install linux like : Gentoo, Ubuntu, Slackware, Fedora, Mandriva, Redhat, Debian n Gnemo.
3. How to create Squidd
4. How to create Proxy
5. How to create perl
6. How to upload file in cpanel or from cgi-telnet
7. All bout programs like : VB, Payroll, Clipper, Autocad, Deplhi, C++ etc
8. etc...( still much again i will post those in here..)
just wait...
#1 posting - bout command
| Command | Description |
| a2p | Creates a Perl script from an awk script. |
| ac | Prints statistics about users' connect time. |
| alias | Create a name for another command or long command string. |
| ar | Maintain portable archive or library. |
| arch | Display the architecture of the current host. |
| arp | Manipulate the system ARP cache. |
| as | An assembler. |
| at | Command scheduler. |
| awk | Awk script processing program. |
| basename | Deletes any specified prefix from a string. |
| bash | Command Bourne interpreter |
| bc | Calculator. |
| bdiff | Compare large files. |
| bfs | Editor for large files. |
| bg | Continues a program running in the background. |
| biff | Enable / disable incoming mail notifications. |
| break | Break out of while, for, foreach, or until loop. |
| bs | Battleship game. |
| bye | Alias often used for the exit command. |
| cal | Calendar |
| calendar | Display appointments and reminders. |
| cancel | Cancels a print job. |
| cat | View and/or modify a file. |
| cc | C compiler. |
| cd | Change directory. |
| chdir | Change directory. |
| checkeq | Language processors to assist in describing equations. |
| checknr | Check nroff and troff files for any errors. |
| chfn | Modify your own information or if super user or root modify another users information. |
| chgrp | Change a groups access to a file or directory. |
| chkey | Change the secure RPC key pair. |
| chmod | Change the permission of a file. |
| chown | Change the ownership of a file. |
| chsh | Change login shell. |
| cksum | Display and calculate a CRC for files. |
| clear | Clears screen. |
| cls | Alias often used to clear a screen. |
| cmp | Compare files. |
| col | Reverse line-feeds filter. |
| comm | Compare files and select or reject lines that are common. |
| compress | Compress files on a computer. |
| continue | Break out of while, for, foreach, or until loop. |
| copy | Copy files. |
| cp | Copy files. |
| cpio | Creates archived CPIO files. |
| crontab | Create and list files that you wish to run on a regular schedule. |
| csh | Execute the C shell command interpreter |
| csplit | Split files based on context. |
| ctags | Create a tag file for use with ex and vi. |
| cu | Calls or connects to another Unix system, terminal or non-Unix system. |
| curl | Transfer a URL. |
| cut | Cut out selected fields of each line of a file. |
| date | Tells you the date and time in Unix. |
| dc | An arbitrary precision arithmetic package. |
| df | Display the available disk space for each mount. |
| deroff | Removes nroff/troff, tbl, and eqn constructs. |
| dhclient | Dynamic Host Configuration Protocol Client. |
| diff | Displays two files and prints the lines that are different. |
| dig | DNS lookup utility. |
| dircmp | Lists the different files when comparing directories. |
| dirname | Deliver portions of path names. |
| dmesg | Print or control the kernel ring buffer. |
| dos2unix | Converts text files between DOS and Unix formats. |
| dpost | Translates files created by troff into PostScript. |
| du | Tells you how much space a file occupies. |
| echo | Displays text after echo to the terminal. |
| ed | Line oriented file editor. |
| edit | Text editor. |
| egrep | Search a file for a pattern using full regular expressions. |
| elm | Program command used to send and receive e-mail. |
| emacs | Text editor. |
| enable | Enables / Disables LP printers. |
| env | Displays environment variables. |
| eqn | Language processors to assist in describing equations. |
| ex | Line-editor mode of the vi text editor. |
| exit | Exit from a program, shell or log you out of a Unix network. |
| expand | Expand copies of file s. |
| expr | Evaluate arguments as an expression. |
| fc | The FC utility lists or edits and re-executes, commands previously entered to an interactive sh. |
| fg | Continues a stopped job by running it in the foreground |
| fgrep | Search a file for a fixed-character string. |
| file | Tells you if the object you are looking at is a file or if it is a directory. |
| find | Finds one or more files assuming that you know their approximate filenames. |
| findsmb | List info about machines that respond to SMB name queries on a subnet. |
| finger | Lists information about the user. |
| fmt | Simple text formatters. |
| fold | Filter for folding lines. |
| for | Shell built-in functions to repeatedly execute action(s) for a selected number of times. |
| foreach | Shell built-in functions to repeatedly execute action(s) for a selected number of times. |
| fromdos | Converts text files between DOS and Unix formats. |
| fsck | Check and repair a Linux file system. |
| ftp | Enables ftp access to another terminal. |
| getfacl | Display discretionary file information. |
| gprof | The gprof utility produces an execution profile of a program. |
| grep | Finds text within a file. |
| groupadd | Creates a new group account. |
| groupdel | Enables a super user or root to remove a group. |
| groupmod | Enables a super user or root to modify a group. |
| gunzip | Expand compressed files. |
| gview | A programmers text editor. |
| gvim | A programmers text editor. |
| gzip | Compress files. |
| halt | Stop the computer. |
| hash | Remove internal hash table. |
| hashstat | Display the hash stats. |
| head | Displays the first ten lines of a file, unless otherwise stated. |
| help | If computer has online help documentation installed this command will display it. |
| history | Display the history of commands typed. |
| host | DNS lookup utility. |
| hostid | Prints the numeric identifier for the current host. |
| hostname | Set or print name of current host system. |
| id | Shows you the numeric user and group ID on BSD. |
| ifconfig | Sets up network interfaces. |
| ifdown | take a network interface down |
| ifup | bring a network interface up |
| isalist | Display the native instruction sets executable on this platform. |
| jobs | List the jobs currently running in the background. |
| join | Joins command forms together. |
| keylogin | Decrypt the user's secret key. |
| kill | Cancels a job. |
| ksh | Korn shell command interpreter. |
| ld | Link-editor for object files. |
| ldd | List dynamic dependencies of executable files or shared objects. |
| less | Opposite of the more command. |
| lex | Generate programs for lexical tasks. |
| link | Calls the link function to create a link to a file. |
| ln | Creates a link to a file. |
| lo | Allows you to exit from a program, shell or log you out of a Unix network. |
| locate | List files in databases that match a pattern. |
| login | Signs into a new system. |
| logname | Returns users login name. |
| logout | Logs out of a system. |
| lp | Prints a file on System V systems. |
| lpadmin | Configure the LP print service. |
| lpc | Line printer control program. |
| lpq | Lists the status of all the available printers. |
| lpr | Submits print requests. |
| lprm | Removes print requests from the print queue. |
| lpstat | Lists status of the LP print services. |
| ls | Lists the contents of a directory. |
| mach | Display the processor type of the current host. |
| One of the ways that allows you to read/send E-Mail. | |
| mailcompat | Provide SunOS 4.x compatibility for the Solaris mailbox format. |
| mailx | Mail interactive message processing system. |
| make | Executes a list of shell commands associated with each target. |
| man | Display a manual of a command. |
| mesg | Control if non-root users can send text messages to you. |
| mii-tool | View, manipulate media-independent interface status. |
| mkdir | Create a directory. |
| mkfs | Build a Linux file system, usually a hard disk partition. |
| more | Displays text one screen at a time. |
| mount | Disconnects a file systems and remote resources. |
| mt | Magnetic tape control. |
| mv | Renames a file or moves it from one directory to another directory. |
| nc | TCP/IP swiss army knife. |
| neqn | Language processors to assist in describing equations. |
| netstat | Shows network status. |
| newalias | Install new elm aliases for user and/or system. |
| newform | Change the format of a text file. |
| newgrp | Log into a new group. |
| nice | Invokes a command with an altered scheduling priority. |
| niscat | Display NIS+ tables and objects. |
| nischmod | Change access rights on a NIS+ object. |
| nischown | Change the owner of a NIS+ object. |
| nischttl | Change the time to live value of a NIS+ object. |
| nisdefaults | Display NIS+ default values. |
| nisgrep | Utilities for searching NIS+ tables. |
| nismatch | Utilities for searching NIS+ tables. |
| nispasswd | Change NIS+ password information. |
| nistbladm | NIS+ table administration command. |
| nmap | Network exploration tool and security / port scanner. |
| nohup | Runs a command even if the session is disconnected or the user logs out. |
| nroff | Formats documents for display or line-printer. |
| nslookup | Queries a name server for a host or domain lookup. |
| on | Execute a command on a remote system, but with the local environment. |
| onintr | Shell built-in functions to respond to (hardware) signals. |
| optisa | Determine which variant instruction set is optimal to use. |
| pack | Shrinks file into a compressed file. |
| pagesize | Display the size of a page of memory in bytes, as returned by getpagesize. |
| passwd | Allows you to change your password. |
| paste | Merge corresponding or subsequent lines of files. |
| pax | Read / write and writes lists of the members of archive files and copy directory hierarchies. |
| pcat | Compresses file. |
| perl | Perl is a programming language optimized for scanning arbitrary text files, extracting information from those text files. |
| pg | Files perusal filters for CRTs. |
| pgrep | Examine the active processes on the system and reports the process IDs of the processes |
| pico | Simple and very easy to use text editor in the style of the Pine Composer. |
| pine | Command line program for Internet News and Email. |
| ping | Sends ICMP ECHO_REQUEST packets to network hosts. |
| pkill | Examine the active processes on the system and reports the process IDs of the processes |
| poweroff | Stop the computer. |
| pr | Formats a file to make it look better when printed. |
| priocntl | Display's or set scheduling parameters of specified process(es) |
| printf | Write formatted output. |
| ps | Reports the process status. |
| pvs | Display the internal version information of dynamic objects within an ELF file. |
| pwd | Print the current working directory. |
| quit | Allows you to exit from a program, shell or log you out of a Unix network. |
| rcp | Copies files from one computer to another computer. |
| reboot | Stop the computer. |
| red | Line oriented file editor. |
| rehash | Recomputes the internal hash table of the contents of directories listed in the path. |
| remsh | Runs a command on another computer. |
| repeat | Shell built-in functions to repeatedly execute action(s) for a selected number of times. |
| rgview | A programmers text editor. |
| rgvim | A programmers text editor. |
| rlogin | Establish a remote connection from your terminal to a remote machine. |
| rm | Deletes a file without confirmation (by default). |
| rmail | One of the ways that allows you to read/send E-Mail. |
| rmdir | Deletes a directory. |
| rn | Reads newsgroups. |
| route | Show / manipulate the IP routing table. |
| rpcinfo | Report RPC information. |
| rsh | Runs a command on another computer. |
| rsync | Faster, flexible replacement for rcp. |
| rview | A programmers text editor. |
| rvim | A programmers text editor. |
| s2p | Convert a sed script into a Perl script. |
| sag | Graphically displays the system activity data stored in a binary data file by a previous sar run. |
| sar | Displays the activity for the CPU. |
| script | Records everything printed on your screen. |
| sdiff | Compares two files, side-by-side. |
| sed | Allows you to use pre-recorded commands to make changes to text. |
| sendmail | Sends mail over the Internet. |
| set | Set the value of an environment variable. |
| setenv | Set the value of an environment variable. |
| setfacl | Modify the Access Control List (ACL) for a file or files. |
| settime | Change file access and modification time. |
| sftp | Secure file transfer program. |
| sh | Runs or processes jobs through the Bourne shell. |
| shred | Delete a file securely, first overwriting it to hide its contents. |
| shutdown | Turn off the computer immediately or at a specified time. |
| sleep | Waits a x amount of seconds. |
| slogin | OpenSSH SSH client (remote login program). |
| smbclient | An ftp-like client to access SMB/CIFS resources on servers. |
| sort | Sorts the lines in a text file. |
| spell | Looks through a text file and reports any words that it finds in the text file that are not in the dictionary. |
| split | Split a file into pieces. |
| stat | Display file or filesystem status. |
| stop | Control process execution. |
| strip | Discard symbols from object files. |
| stty | Sets options for your terminal. |
| su | Become super user or another user. |
| sysinfo | Get and set system information strings. |
| sysklogd | Linux system logging utilities. |
| tabs | Set tabs on a terminal. |
| tail | Delivers the last part of the file. |
| talk | Talk with other logged in users. |
| tac | Concatenate and print files in reverse. |
| tar | Create tape archives and add or extract files. |
| tbl | Preprocessor for formatting tables for nroff or troff. |
| tcopy | Copy a magnetic tape. |
| tcpdump | Dump traffic on a network. |
| tee | Read from an input and write to a standard output or file. |
| telnet | Uses the telnet protocol to connect to another remote computer. |
| time | Used to time a simple command. |
| timex | The timex command times a command; reports process data and system activity. |
| todos | Converts text files between DOS and Unix formats. |
| top | Display Linux tasks. |
| touch | Change file access and modification time. |
| tput | Initialize a terminal or query terminfo database. |
| tr | Translate characters. |
| traceroute | Print the route packets take to network host. |
| troff | Typeset or format documents. |
| ul | Reads the named filenames or terminal and does underlining. |
| umask | Get or set the file mode creation mask. |
| unalias | Remove an alias. |
| unhash | Remove internal hash table. |
| uname | Print name of current system. |
| uncompress | Uncompressed compressed files. |
| uniq | Report or filter out repeated lines in a file. |
| unmount | Crates a file systems and remote resources. |
| unpack | Expands a compressed file. |
| untar | Create tape archives and add or extract files. |
| until | Execute a set of actions while/until conditions are evaluated TRUE. |
| useradd | Create a new user or updates default new user information. |
| userdel | Remove a users account. |
| usermod | Modify a users account. |
| vacation | Reply to mail automatically. |
| vedit | Screen-oriented (visual) display editor based on ex. |
| vgrind | Grind nice program listings |
| vi | Screen-oriented (visual) display editor based on ex. |
| vim | A programmers text editor. |
| view | A programmers text editor. |
| w | Show who is logged on and what they are doing. |
| wait | Await process completion. |
| wc | Displays a count of lines, words, and characters in a file |
| whereis | Locate a binary, source, and manual page files for a command. |
| while | Repetitively execute a set of actions while/until conditions are evaluated TRUE. |
| which | Locate a command. |
| who | Displays who is on the system. |
| whois | Internet user name directory service. |
| write | Send a message to another user. |
| X | Execute the X windows system. |
| xfd | Display all the characters in an X font. |
| xlsfonts | Server font list displayer for X. |
| xset | User preference utility for X. |
| xterm | Terminal emulator for X. |
| xrdb | X server resource database utility. |
| yacc | Short for yet another compiler-compiler, yacc is a compiler. |
| yes | Repeatedly output a line with all specified STRING(s), or 'y'. |
| yppasswd | Changes network password in the NIS database. |
| zcat | Compress files. |
Subscribe to:
Posts (Atom)